Business Email Compromise
BEC
Business Email Compromise (BEC) is when an attacker hacks into a corporate email account and impersonates the real owner to defraud a company, consumer, partners, and employees into sending money or sensitive data to the hacker’s account. (Zhang, 2018). BEC is also known as the “man-in-the-email” attack — this means that two parties think they are talking only with each other, but a hacker is listening in on the conversation. The hacker could possibly change the communication of the conversation on both sides. Here’s how: first, the hacker tries to gain access to executive email accounts. The hacker can then remain undetected as s/he changes the reply address, so the executive will not be alerted until the scam is complete.
Three Hacker Tools
There are three main tools hackers use in order to target and exploit their victims. The first tool is Spoofing email accounts or websites. Spoofing is considered to be slight variations on legitimate URL’s or email addresses to fool victims into thinking that they are authentic (FBI, 2017). The hacker redirects you to a website or email that they are controlling, to gain personal or private information.
- Spoofed email addresses
Original: John.Smith@johnsonllc.com
Spoof: John.Smitth@johnsonllc.com
The Second tool hackers use is Spear Phishing. Spear-Phishing is when a fraudulent email is considered to be trustworthy and prompts the victim to reveal confidential information (FBI, 2017). First, look at the sender’s email address, especially if they are asking you to open up an attachment within the email. Usually, the cybercriminal will use a public email address, often as close to the original as possible. Make sure to check the authenticity of the email by paying close attention to spelling, added letters or symbols. Phishing emails will be off by a letter or number. When looking in an email from a company, bank, or colleague, look for the company name in the email address.
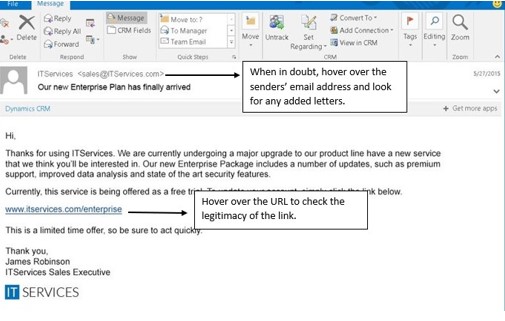
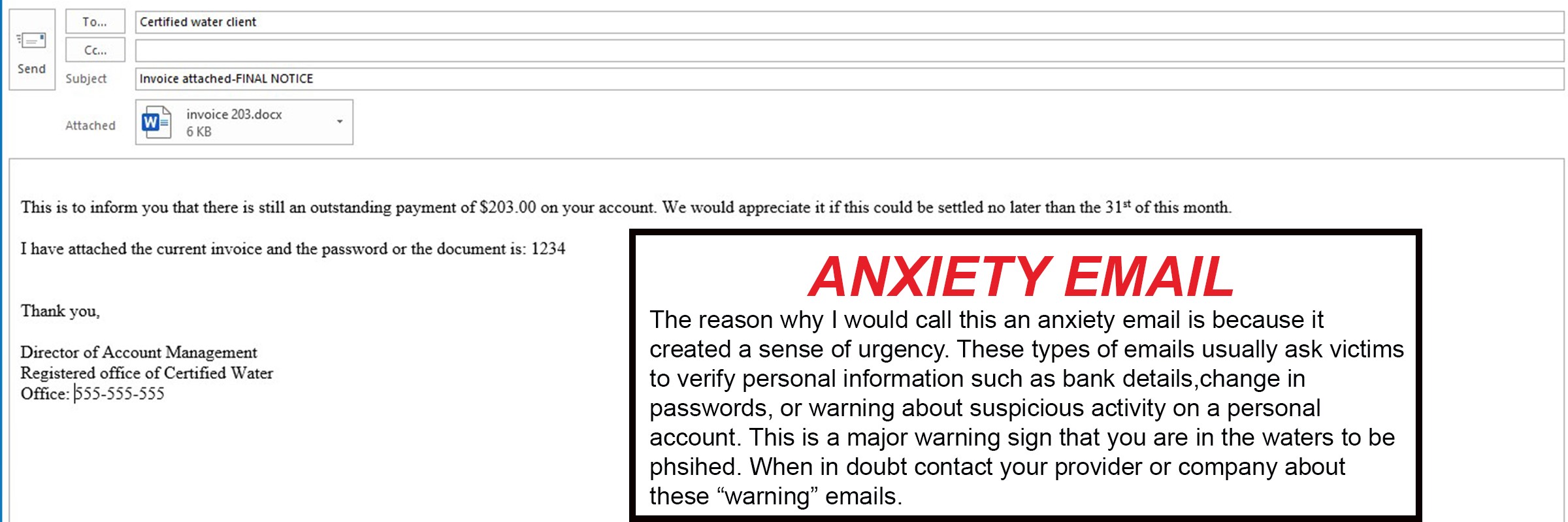
The third and final tool used for hackers is — you guessed it – MALWARE. Malware is used to infiltrate a company’s network to gain access to legitimate email threads about billing or invoices (FBI, 2017). Malware also allows cybercriminals to have undetected access to victims’ data, including passwords and financial account information. If you receive an email with a document attached, do not open it! Wait until you have checked the authenticity of the email. When a stranger asks you to download a document, it usually means that there is malware attached to it. When malware is attached to documents, they can harm your computer and steal all your personal credentials.
BEC Billion Dollar Enterprise
According to the Symantec Security Response Team (2019), BEC scams have amounted to $1.3 billion in 2018, which is double the losses in 2017. Aggregate losses from internet theft, fraud, and exploitation have reached an all-time high at $2.7 billion, and half of this figure was due to BEC (Symantec Security Response Team, 2019). On average, the BEC volume in 2018 was 85,816. From January 2019 to March 2019, the BEC daily volume was at 128,700, 50% higher than 2018. In the past 12 months, over 6,000 business was targeted by hackers every month. Currently, the U.S. is standing at the number one victim region of BEC in the past 12 months. BEC scammers are targeting small, medium and large-sized companies. Between May 2018 and July 2019, there was a 100% increase in identified global exposed losses (Sussman, 2019).
Groff Networks
As tricky as cybercriminals are, we here at Groff NetWorks see them every day. We implement phishing training for our employees, clients, and services to regularly phish test. We designed our test for the “clickers” that are potentially in your company. We consider ourselves to be caring, responsive, friendly and honest – that is our recipe for helping our users (your employees!) to stay safe from hackers.
References:
Egan, G. (2018, July 25). $12.5 Billion Lost in BEC Attacks, FBI Reports. Retrieved December 20, 2019, from https://www.wombatsecurity.com/blog/12.5-billion-lost-in-bec-attacks-fbi-reports.
FBI. (2017, February 27). Business E-Mail Compromise. Retrieved December 20, 2019, from https://www.fbi.gov/news/stories/business-e-mail-compromise-on-the-rise.
Sussman, B. (2019, September 11). Business Email Compromise Losses Jump 100%. Retrieved December 20, 2019, from https://www.secureworldexpo.com/industry-news/new-business-email-compromise-statistics-bec
Symantec Security Response Team. (2019, July 23). BEC Scams Remain a Billion-Dollar Enterprise, Targeting 6K Businesses Monthly. Retrieved December 20, 2019, from https://www.symantec.com/blogs/threat-intelligence/bec-scams-trends-and-themes-2019
Zhang, E. (2018, September 12). What is Business E-mail Compromise? How It Works, Best Practices for Protection, and More. Retrieved December 20, 2019, from https://digitalguardian.com/blog/what-business-e-mail-compromise-how-it-works-best-practices-and-more.
